Configuring Credential Types
Credential types enable organizations to map users to specific certificates and card policies within the CMS. Additionally, organizations can specify qualification rules to ensure users meet certain business rules before they can be assigned to a specific credential type. The feature is useful if the organization wants to segment different users for different types of credentials. For example, users within a general access group may receive credentials with low assurance certificates whereas users within an administrator group could receive high assurance certificates.
Requirements:
Before assigning a credential type, a card policy must exist within the CMS. Also, there is a one to one relationship between the IDMS credential type and the CMS card policy. Therefore, the IDMS credential types cannot share CMS card policies.
Creating an IDMS Credential Type
The steps below provide the procedure for creating a credential type:
Procedure | Example | |
|---|---|---|
| 1 | Authenticate to the IDMS as a system administrator. | |
| 2 | Go to Administration, and then click on the Credential Types link. |  |
| 3 | When the Credential Policy Management window appears, press Create a new credential policy. |  |
| 4 | Credential Policy Name: Name of the policy. | 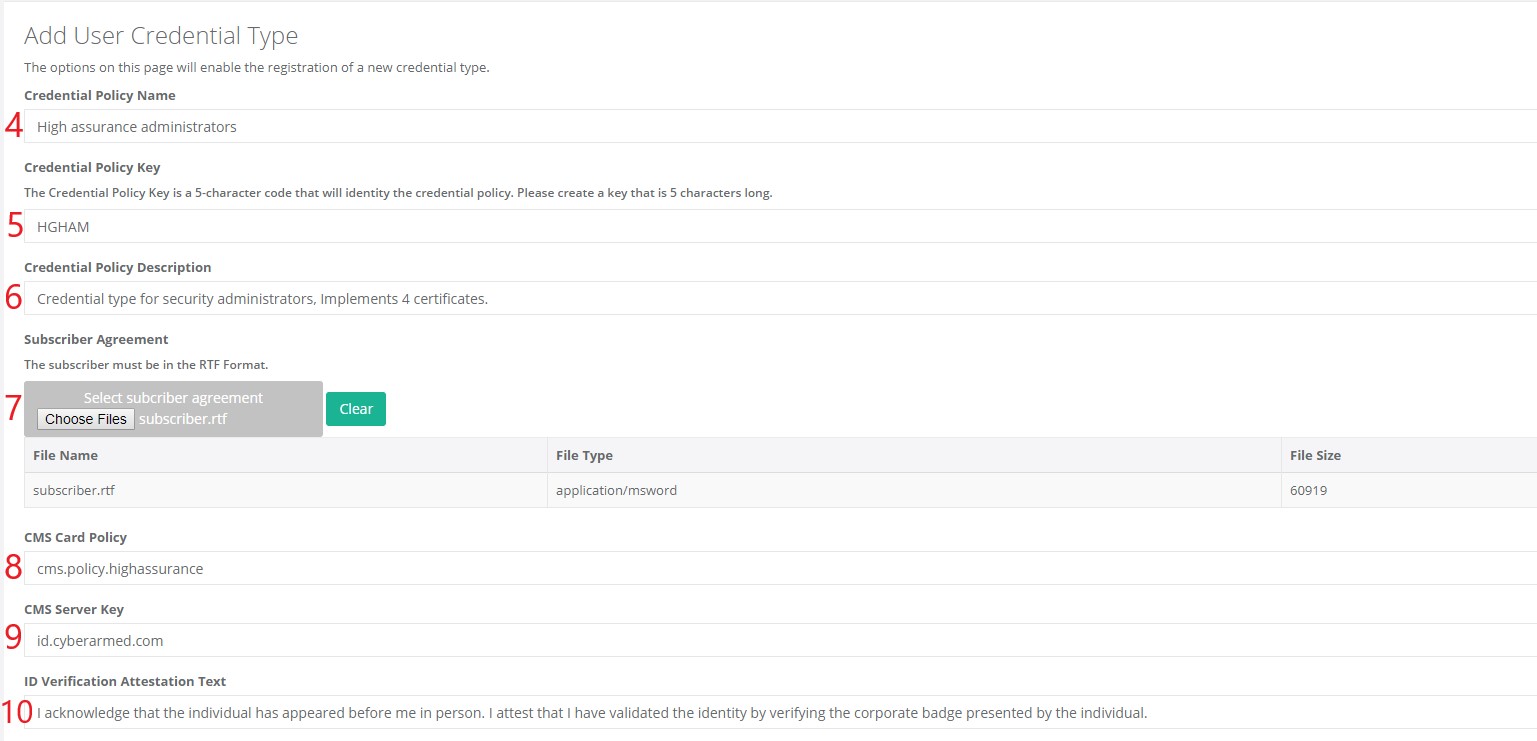 |
| 5 | Credential Policy Key: A 5 character abbreviation of the credential policy. | |
| 6 | Credential Policy Description: Description of the purpose of the credential policy. | |
| 7 | Subscriber Agreement: The Microsoft RTF document listing the subscriber agreement text. This document will be downloaded the workstation clients. | |
| 8 | CMS Card Policy: The CMS card policy this credential type maps to. | |
| 9 | CMS Server Key: The DNS Name of the CMS Server. | |
| 10 | ID Verification Attestation Text : This is the text the operator will agree to when they they credentialing a user. Example: When the ID Verfication Attestation Text is set in the IDMS, the text will appear for the operator to read and agree to. 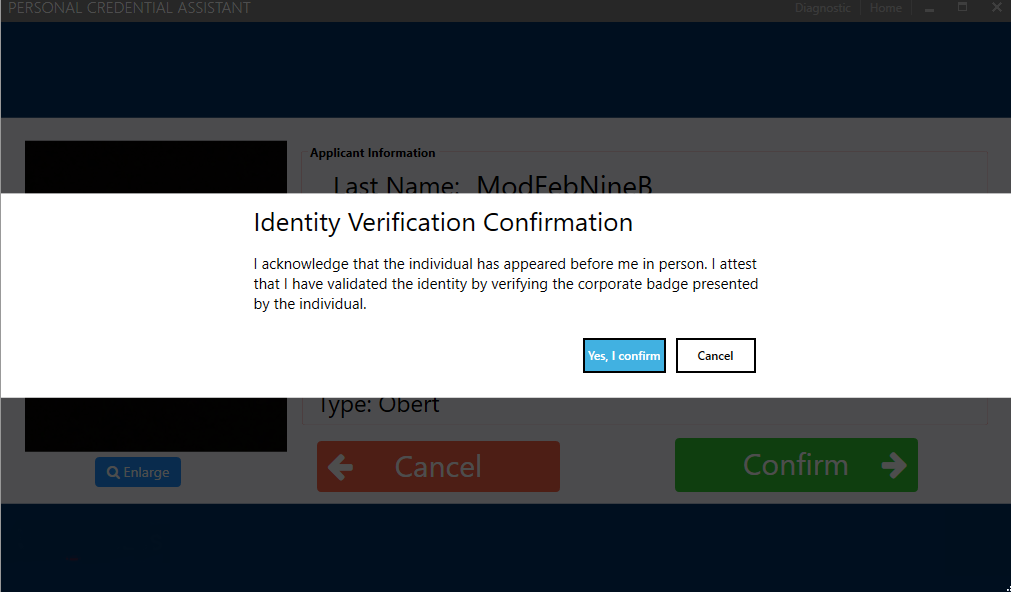 | |
| 11 | Require Subscriber Agreement: Specifies whether the cardholder (not operator) will perform a digital signature after their credential has been issued. | 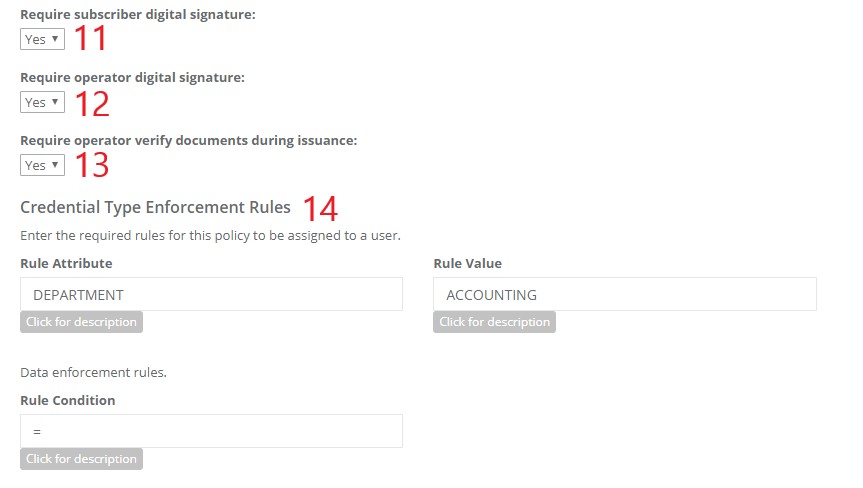 |
| 12 | Require Operator Digital Signature: Specifies whether the operator will perform a digital signature during the credential issuance process. | |
| 13 | Require operator verify documents during issuance: Specifies whether the operator will verify documents during the issuance of a credential. | |
| 14 | Credential Type Enforcement Rules: The IDMS can be configured to query additional user information to ensure an applicant qualifies for a credential. For example, if an organization has a rule that the applicant must be the “ACCOUNTING” department, the IDMS can query the LDAP Attribute ‘deparment’ to verify the value is set to “ACCOUNTING” before the credentialing process can continue.
| |
| 15 | Credential Printing Rules The following configurations determine whether the credential should be physically printed. Print Credential: To have the credential printed, select YES. If the credential should not be printed, select NO. Print Layout Definition: This is the print layout filename that provides the physical layout of the printed card. Perform Inline Encoding During Print: If the credential is to be encoding during the print process. *Note: This requires the HID Card Encoding Module attachment. | 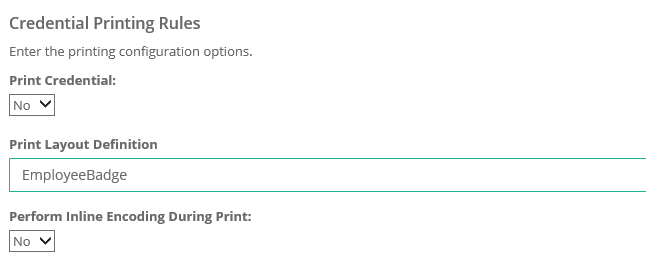 |
| 16 | Name Change Rules To allow the operator to perform a name change, select "Yes". To prevent the operator from performing a name change, select "No" |  |
| 17 | Once the information has been entered and verified, press "Add Policy" to save the Policy. Press Yes to confirm. |  |
| 18 | The IDMS will notify the operator that the credential policy has been added/updated. |  |
| 19 | Once the Policy is created, the administrator can view additional settings by clicking "manage" next to the policy: | |
| 20 | Data Validation Rules The data validation rules specify the criteria an applicant must meet in ordered to quality for the credential type. The rule syntax is: Data attribute condition Data value separated by the “|” character.
| 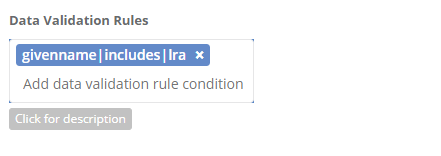 |
| 21 | Credential Policy In Use Status: This defines whether the credential will be enabled or disabled. | |
| 22 | Certificate Authorities: When issuing derived credentials, determines which certificate authority will be used to generate the certificate for the derived credential. | 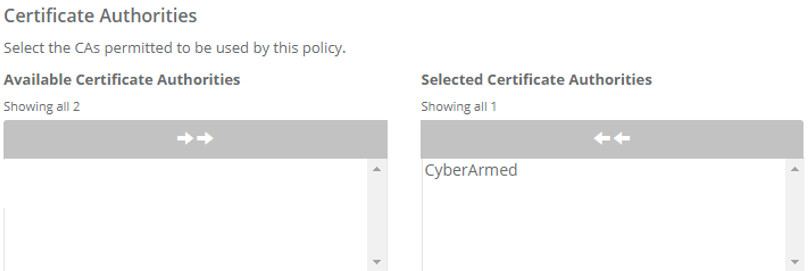 |
| 23 | 3rd Party Credential Enrollment: These security options enable a 3rd party credential holder to authenticate to the system. The configurations are below: Permit Use of Existing Credential For Enrollment: Permits the IDMS to authenticate a 3rd party credential. Credentialing Linking Value: The common value that links the credential and the directory together. This enables the IDMS to look up the identity in an authoritative system to analyze the identity. External Credential Issuing Certificate: The certificate authority that must have issued the 3rd party credential in order for the credential to be verified. | Tip: Setting the External Credential Issuing Certificate: This configuration requires that there be a space after the comma. The configuration also requires no space between the equal sign. 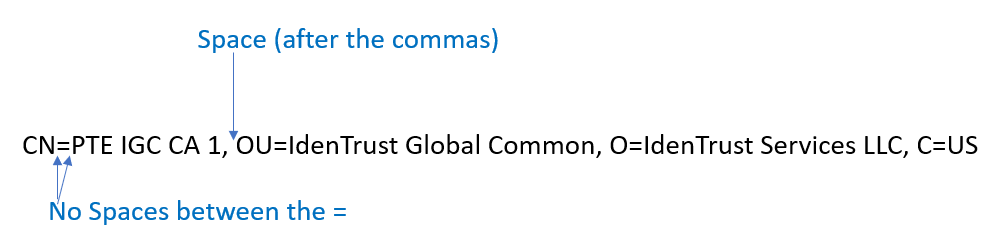 |
| 24 | Background investigation service: The configurations enable a 3rd party background investigation service to enroll and verify the user's identity. Perform Background Investigation Service: Yes, specifies that the applicant will be queued for a background investigation. Background Investigation System: Specifies the service that will perform the background investigation. | 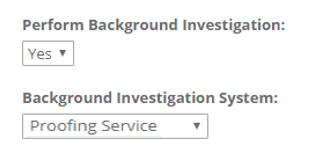 |
