AltSecurityIdentity Certificate Publishing
The Alt Security Identity (altSecurityIdentities) module automatically synchronizes the CMS certificate information with the user’s active directory attribute. The objective is to automate the population of the user’s certificate information into the directory to enable immediate sign on the user’s hardware credential.
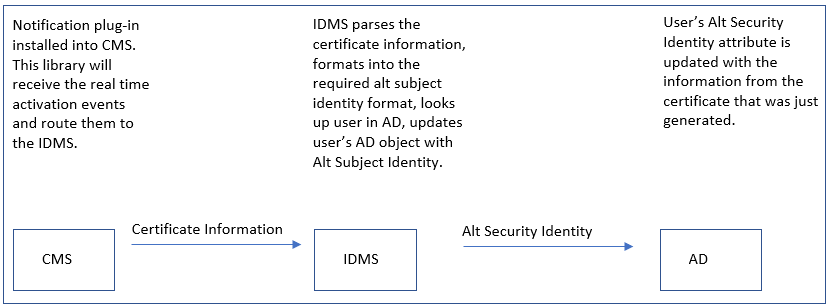
The configuration will update the user's Active Directory's AltSecurityIdentity attribute when their credential is being issued.
Prerequisites
CMS with CMS notification plugin installed
IdExchange Microservice Installed
IDMS installed
Configuration Procedures
Procedure | Example | |
|---|---|---|
| 1 | Enable the "Publish Certificate To Directory" Feature Enable the CMS Event Insert User Feature Enable the External Credential CMS Import Enable the Direct CMS Data Reporting |    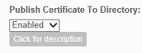 |
| 2 | Configure the following directory settings: LDAP Search Filter = samaccountname LDAP to IDMS Linking key = mail LDAP Attribute To Be Valudated = givenName, sn, mail Try to search for user in IDMS and make sire IDMS can find it. | 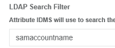 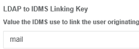 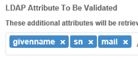 |
| 3 | Perform the CMS Device Profile Mapping. See the section Synching CMS Application ID database with IdExchange Application Database in article Installing and Configuring the IdExchange MicroService For IDMS versions before 1667, use the instructions below. 1: Open the AIMSEE.CONFIGURATION_CFG table and locate the CFG_ID for the PIV_AUTHENTICATION. In the example, the configuration ID is 16 2: Go to the IdExchange.CmsApplicationIdLink table and then enter the CFG_ID and CFG_Description to match. In this example, will add CFG_ID of 16 because that is what CMS had. | |
| 4 | By default, the X509IssuerSerialNumber certificate mapping is used. To use the X509SKI mapping Go to Administration -> System Connections and locate the directory the user is located in. Click configure system and enter X509SKI into the certificate mappings field. Enter the password and then press Update to save the configuration. |  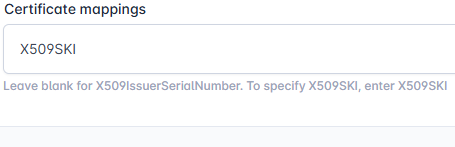 |
| 5 | If the X509SKI mapping is set and the X509IssuerSerialNumber is desired: Go to Administration -> System Connections and locate the directory the user is located in. Click configure system. Scroll to the bottom and locate the Certificate Mappings field. Delete the X509SKI value so that the text box is blank. Enter the correct password to the directory and then press update to save the changes. |  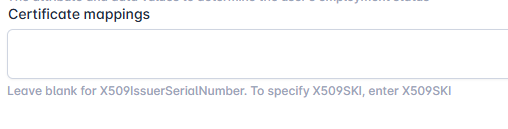 |
To verify the certificate was published:
in the IdExchangeWebApi.txt logs: adding the certificate to the user's directory
